This blog post will show you how to whitelist your GoodAccess gateway IP address in Google Cloud.
Table of contents
- Why choose GoodAccess over Google Cloud native VPN
- How to set up secure access to your Google Cloud with a GoodAccess VPN gateway
Why choose GoodAccess over Google Cloud native VPN
By connecting Google Cloud with your VPN, you can securely include your cloud resources in your distributed virtual network. Google offers a classic VPN and a high-availability (HA) VPN, which uses a pair of tunnels in redundant configuration as a failsafe.
However, Google does not offer a client-to-site VPN. Instead, it has a dedicated zero-trust solution called BeyondCorp, which was originally developed as a more user-friendly alternative to traditional VPNs.
User-friendliness was a valid concern ten years ago, but VPN solutions have advanced since then. What is more, BeyondCorp won’t work outside Google Cloud and is highly cloud-oriented, meaning your 3rd-party and legacy systems may not integrate well.
If you are comfortable with Google as your sole infrastructure provider and all your systems are in the cloud, you may as well go with them (as long as you have the budget). However, if your infrastructure is more diversified, or you want to avoid a vendor lock-in, you might want to explore other options.
GoodAccess is built with a user-first mindset and respects the diversity of your IT infrastructure. You can connect endpoints, clouds, and datacenters with equal ease (without building additional infrastructure), and create your own private and secure environment on the public internet.
How to set up secure access to your Google Cloud with a GoodAccess VPN gateway
To do this, you need a GoodAccess gateway with a static IP address. If you aren’t a GoodAccess user, check out our 14-day trial.
In your VPC network, navigate to the Firewall section and switch to the Create firewall rule tab.
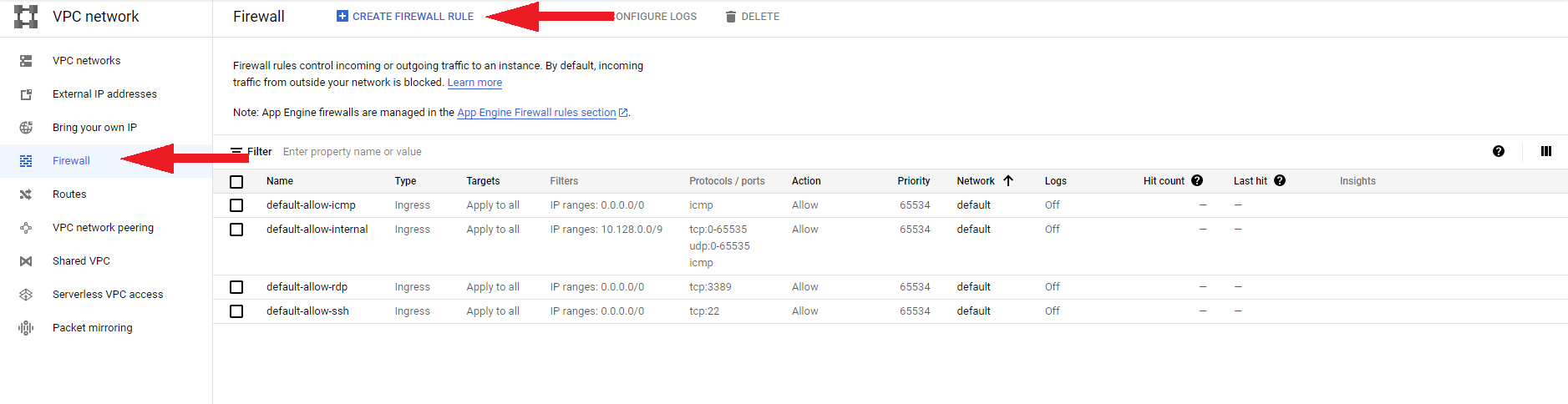
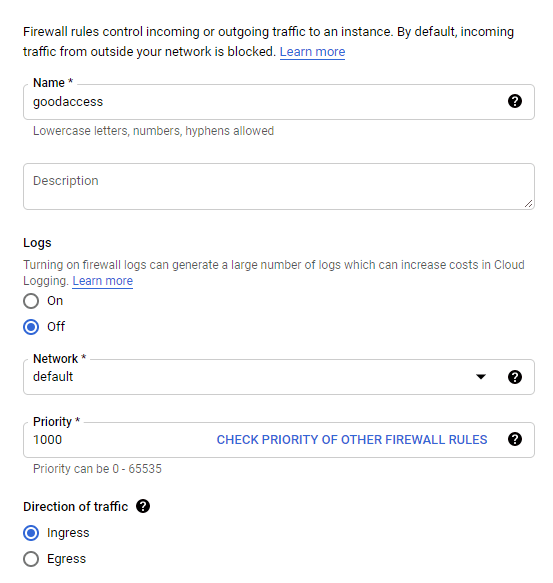
Fill out the following information:
- Name - choose a name; e.g. “GoodAccess”
- Logs - choose if you wish to log the traffic associated with this rule. Note that Google may charge you more if you do.
- Network - choose a network that contains the resources you wish to allow-list
- Priority - leave default
- Direction of traffic - choose Ingress
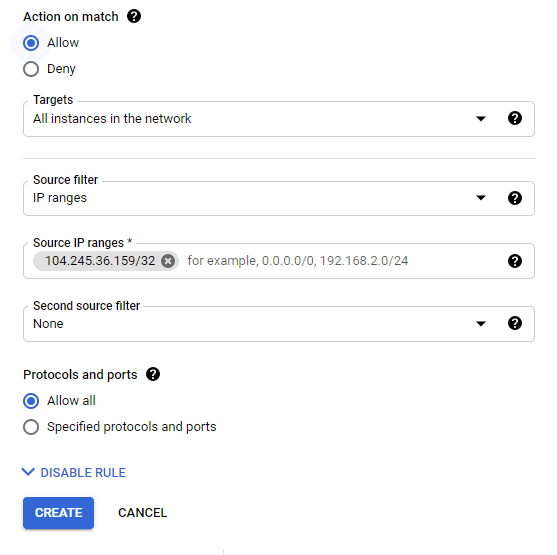
- Actions on match - choose Allow
- Targets - select All instances in the network
- Source filter - select IP ranges
- Source IP ranges - type in the IP address of your GoodAccess gateway followed by “/32” (e.g. 11.22.33.44/32)
- Second source filter - select None
- Protocols and ports - select Allow all
Finally, click Create.
Now you are set. You have allow-listed traffic from your GoodAccess gateway to your Google Cloud.
If you need any help whitelisting your GoodAccess VPN gateway in Google Cloud, contact us. We’re here to help.



















